Unauthenticated Factory Reset Vulnerability in Kiloview E3 Video Encoder
Confirmed for Software Version 1.20.0006
Summary
An unauthenticated API endpoint on Kiloview E3 video encoders allowed remote attackers to trigger a factory reset without any credentials or prior authentication. If the device remained reachable after the reset, it was accessible via default credentials, allowing full dashboard and video feed access.
Timeline
| Date | Action |
|---|---|
| Sunday, April 6th, 2025 | Vulnerability and Exploit Discovered |
| Monday, April 7th, 2025 | CVE Request submitted to MITRE |
| Monday, April 7th, 2025 | Vulnerability and Exploit Disclosed to Vendor |
| Tuesday, April 8th, 2025 | Vendor Acknowledgement and Start of Vendor Triage |
| Monday, July 21st, 2025 | Vendor Patched Vulnerability |
| Friday, July 25th, 2025 | Vulnerability and Exploit Publicly Disclosed |
| Thursday, November 6th, 2025 | CVE Assigned |
Device Discovery
While performing passive recon, I located a Kilview E3 encoder with a publicly exposed login portal.
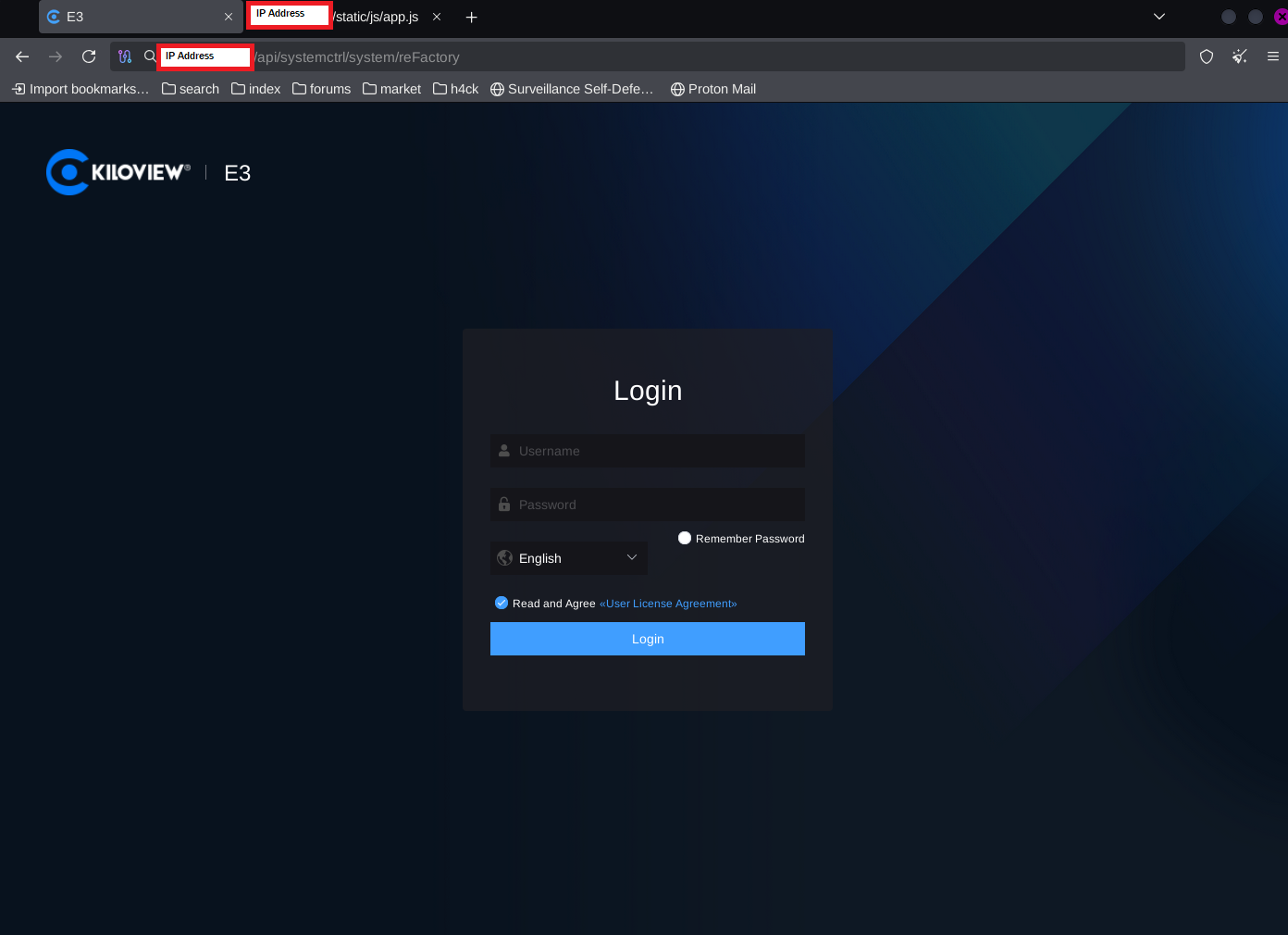
Reconnaissance of Web Interface
Inspecting the login page's source revealed a linked JavaScript file, which most likely was responsible for the web application logic.
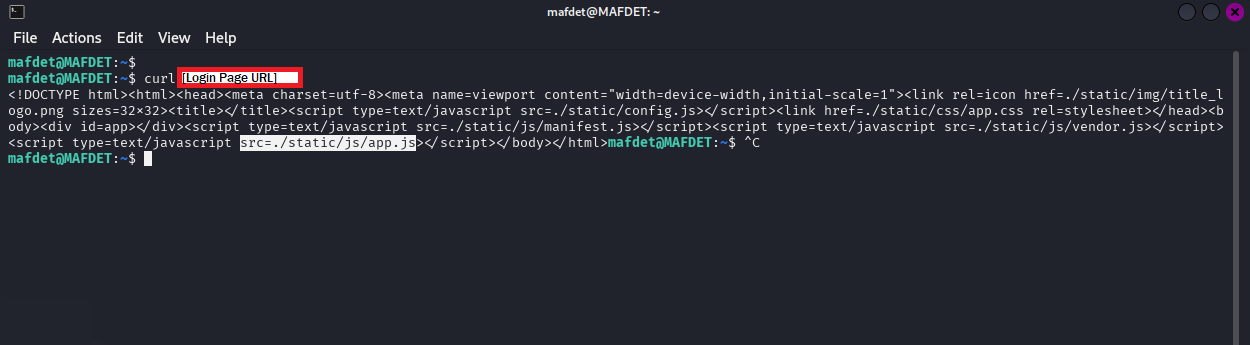
Application Logic and API Discovery
The JavaScript was viewable within a web browser by going to the URL path associated with it. This led me to discover that the web application called API functions through specific URL addresses. The application uses a JavaScript-defined variable proxyUrl, pointing to [device_ip]/api/, as the base for its internal API calls.
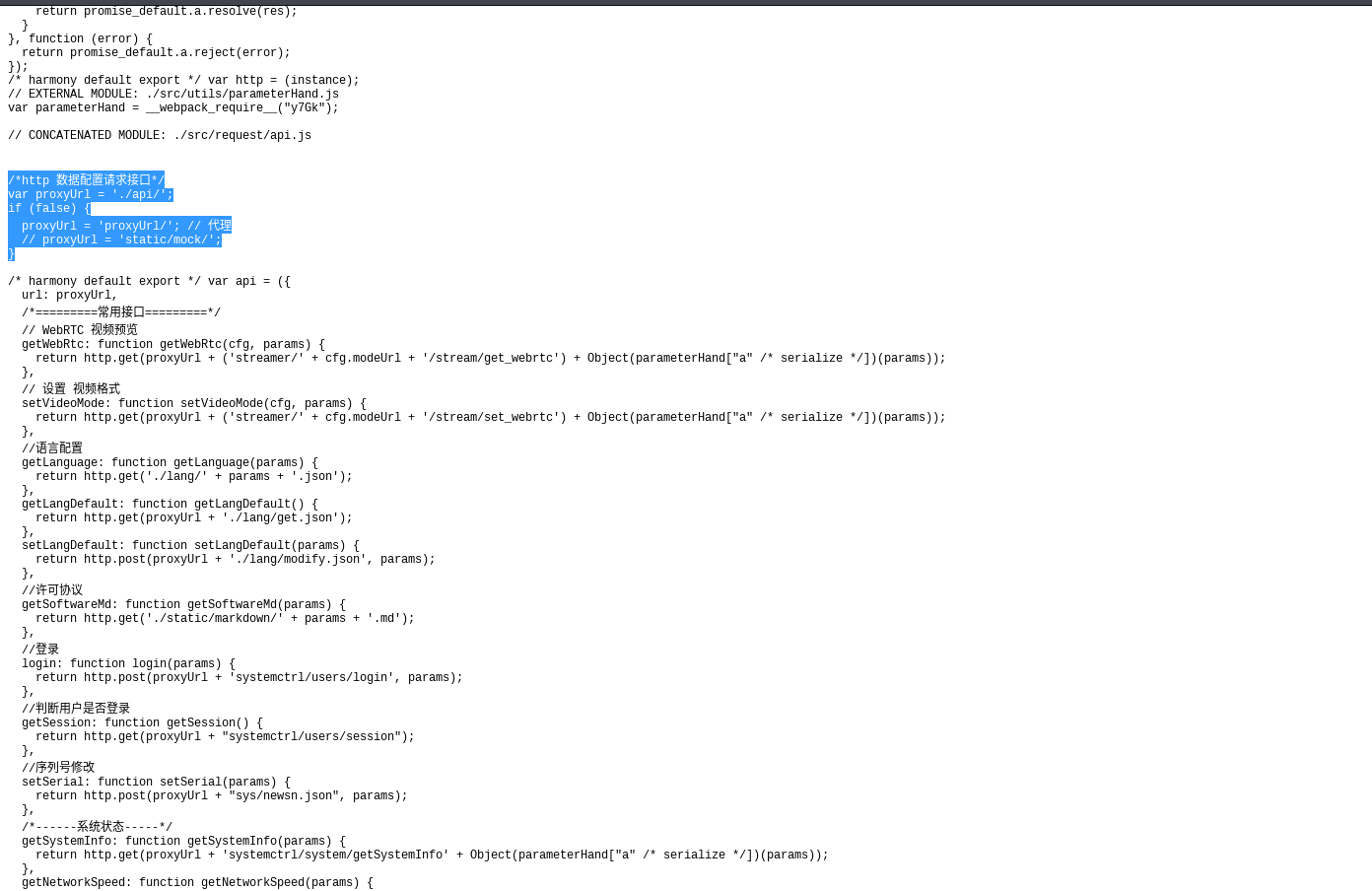
Identification of Vulnerable Endpoints
Following this API URL definition were a series of API functions with their respective URLs to call them. Some functions had parameter values that were handled in their execution. However, functions with no parameters could be called without any authorization, which includes the factory reset function "systemctrl/system/reFactory".
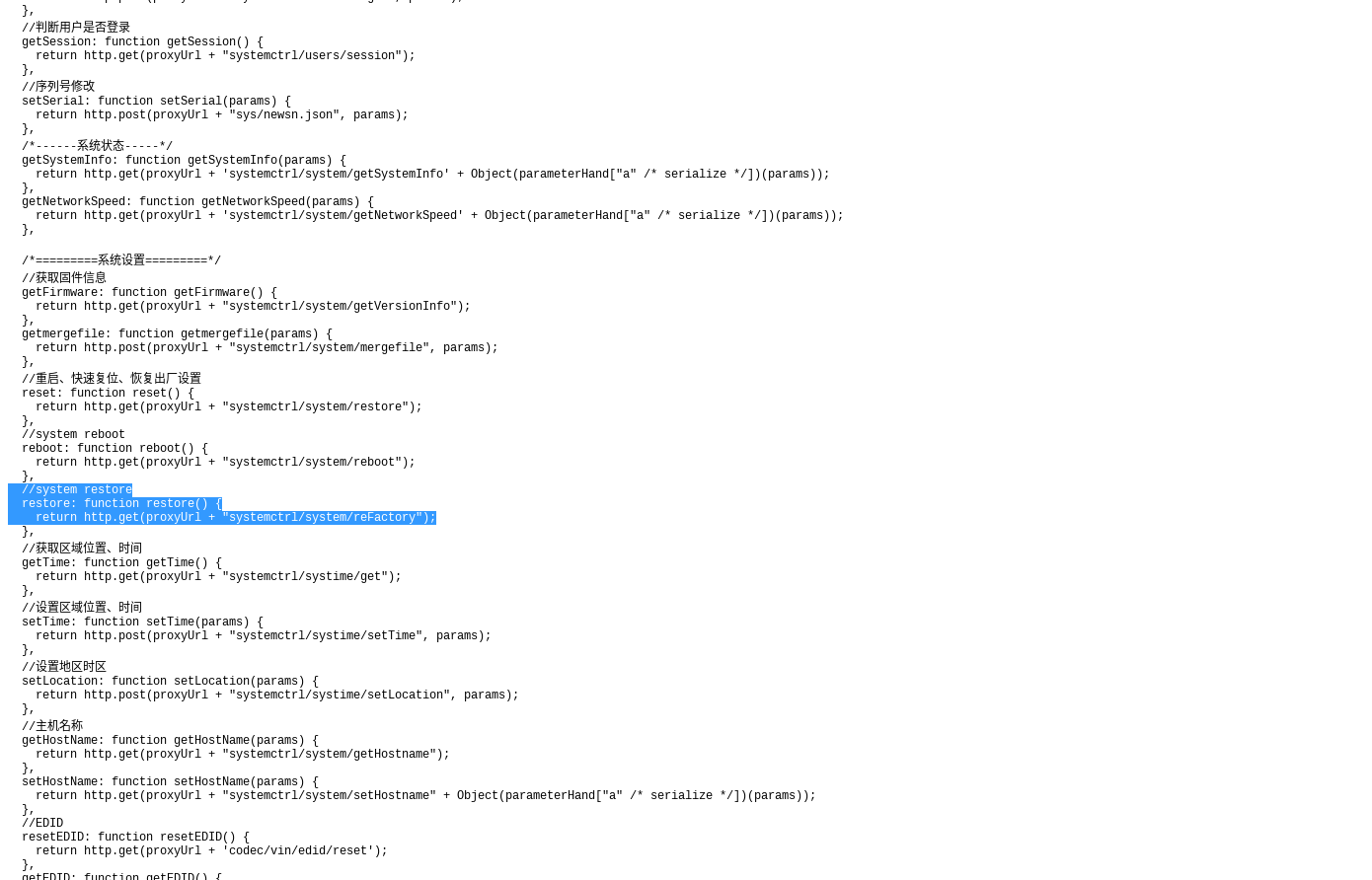
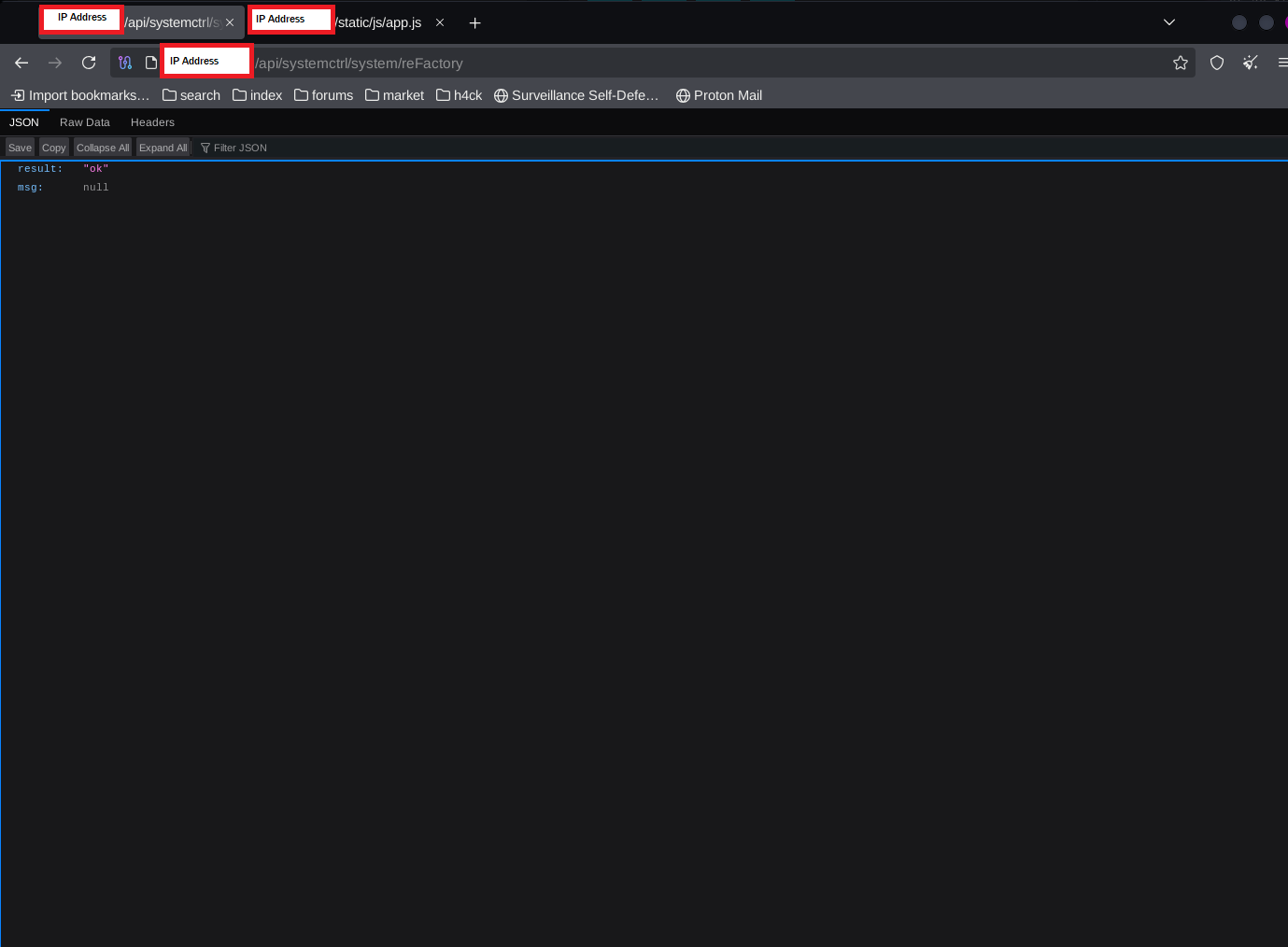
Exploitation
Using the documented endpoint, I crafted a direct API call to the factory reset function. Submitting this request via a browser confirmed successful execution with a status response of result: ok.
Post Exploitation
After factory resetting the device, I have observed two possible outcomes.
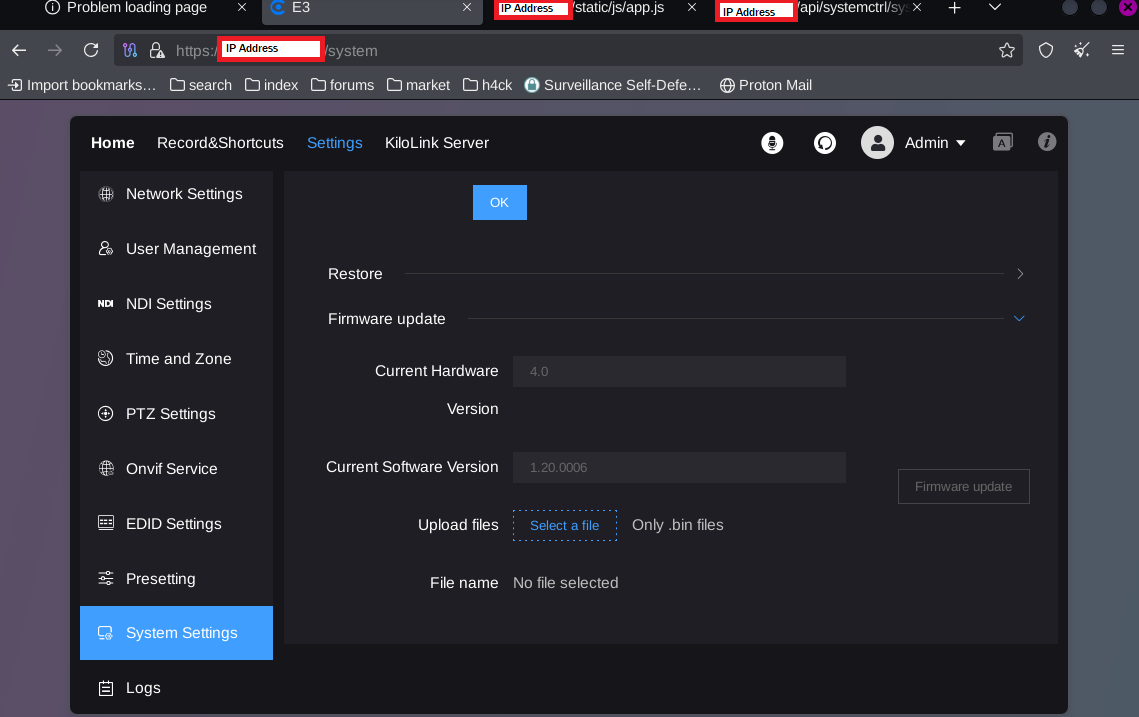
The most common outcome is that the device is no longer reachable post factory reset. Assuming that the reset erases a specific configuration or setting that had initially made it publicly accessible.
The other outcome is that the device is still accessible remotely, which allows the attacker to use the default credentials to log in. Giving the attacker full administrative access to the device.
Skills and Knowledge Developed
- Real-World Reconnaissance and Target Profiling: Conducted passive reconnaissance to identify exposed assets and performed structured analysis of the login page’s front-end logic to uncover embedded references to backend application components.
- API Enumeration Through JavaScript Reverse Engineering: Analyzed obfuscated client-side JavaScript to extract API route structures and access patterns, enabling direct interaction with undocumented endpoints outside of intended workflows.
- Manual Payload Construction and Endpoint Validation: Constructed and executed HTTP requests targeting API endpoints to evaluate authentication controls and endpoint behavior without relying on automated scanners or fuzzers.
- Dynamic Behavior Assessment in Uncontrolled Environments: Observed and documented inconsistent device responses post-exploitation, developing an understanding of how deployment variables and configuration states can affect vulnerability outcomes in production systems.
- Responsible Disclosure Process Execution: Engaged with the vendor directly to report findings, provided reproduction details, and collaborated through the patch lifecycle. Coordinated vulnerability disclosure in parallel with the CVE assignment process to ensure ethical handling.
- Professional Communication and Stakeholder Coordination: Navigated multi-month communication with vendor representatives and maintained clear technical documentation throughout. This reinforced the value of persistence, clarity, and structure when working with external security stakeholders.